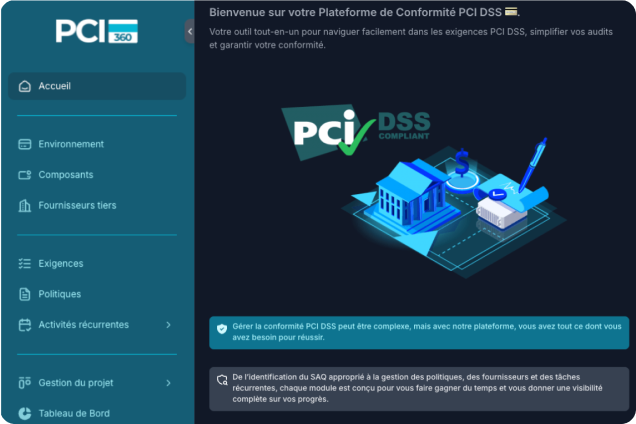
PCI DSS, automatisée par des experts et propulsée par l’IA


PCI360 est la première plateforme intelligente qui simplifie la conformité PCI DSS grâce à une combinaison unique d’automatisation, d’intelligence artificielle et d’outils collaboratifs conçus par des experts du terrain.
-
Réduction de 40 % du temps de préparation à l’audit
-
Automatisation intelligente des tâches et des rappels
-
Supporté par l’IA pour identifier les écarts et définir un plan d’action
Pourquoi PCI DSS est essentiel ?
Qu’est-ce que PCI DSS ?
Réduction des risques de violations de données :
Une non-conformité à PCI DSS (Payment Card Industry Data Security Standard)peut entraîner des sanctions financières et des pertes de réputation.

Obligation
contractuelle :
Toutes les entreprises qui traitent, stockent ou transmettent des données de cartes de clients, doivent respecter cette norme.
Avantage compétitif
Une conformité démontrée inspire la confiance des clients et partenaires.

Automatisez et Simplifiez votre Conformité PCI DSS
Avec PCI360, vous bénéficiez de :
Automatisation
Gagnez du temps sur les tâches récurrentes.
Visibilité
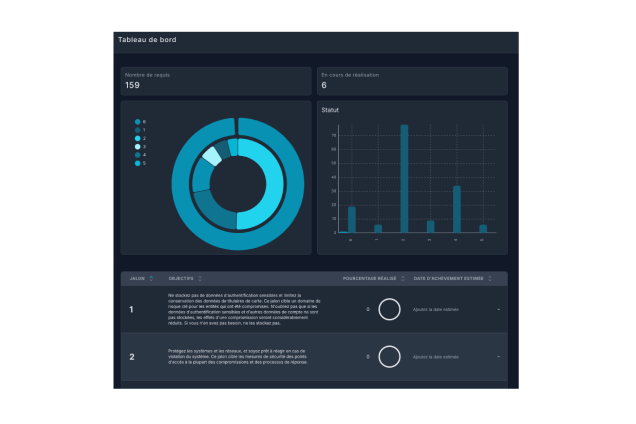
Suivez vos progrès en temps réel.
Collaboration
Travaillez efficacement avec vos équipes et partenaires.
PCI360 est une plateforme SaaS intuitive et complète conçue pour :
Centraliser toutes vos activités de conformité PCI DSS.
Réduire les efforts manuels grâce à l’automatisation.
Améliorer la collaboration entre vos équipes internes et vos partenaires externes.
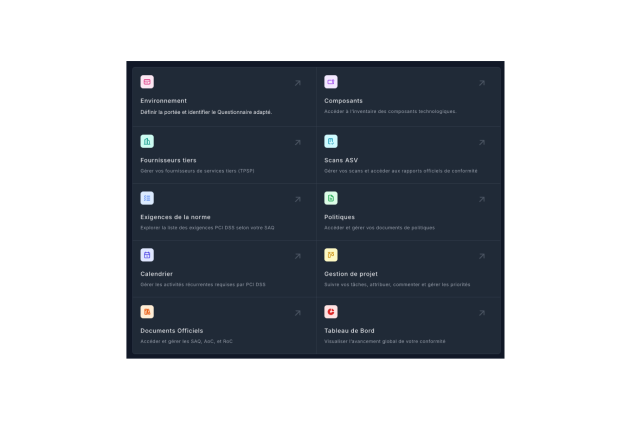
Notre plateforme PCI 360







Des outils puissants pour chaque
étape de votre conformité PCI DSS
Fonctionnalités principales
01
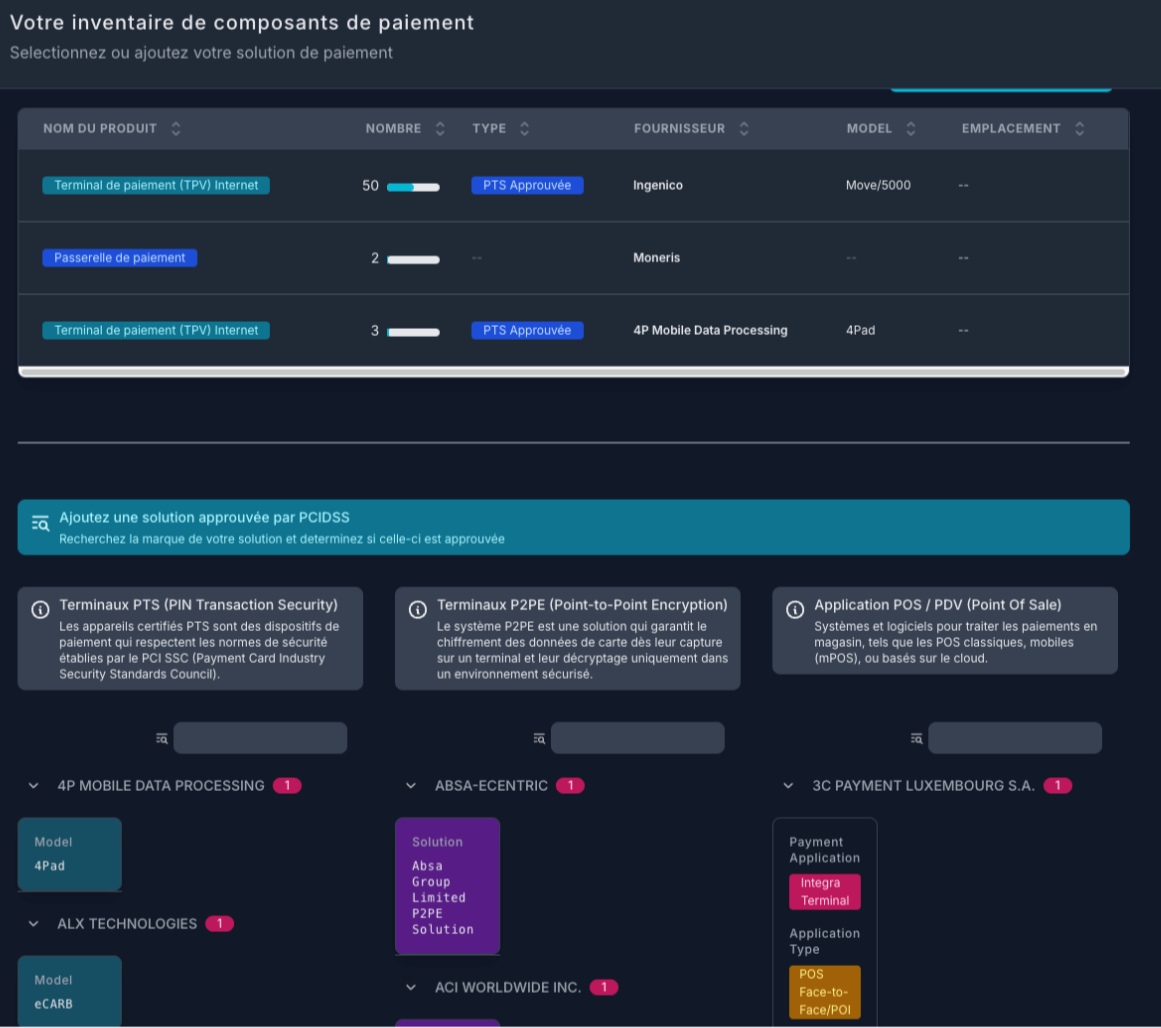
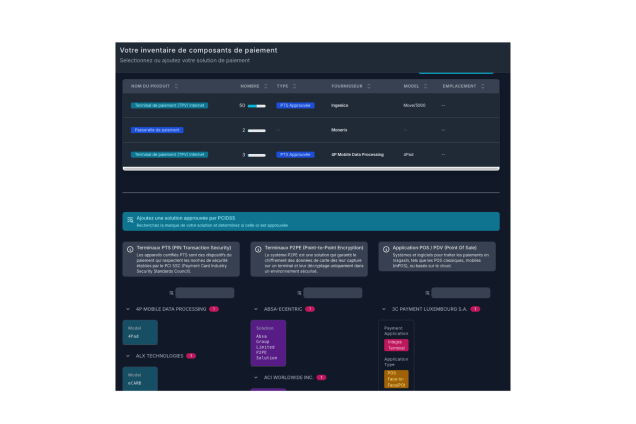
Gestion des SAQ (Self-Assessment Questionnaires)
Identifiez le SAQ approprié à votre organisation grâce à notre assistant intelligent.
Centralisez toutes vos réponses avec traçabilité.
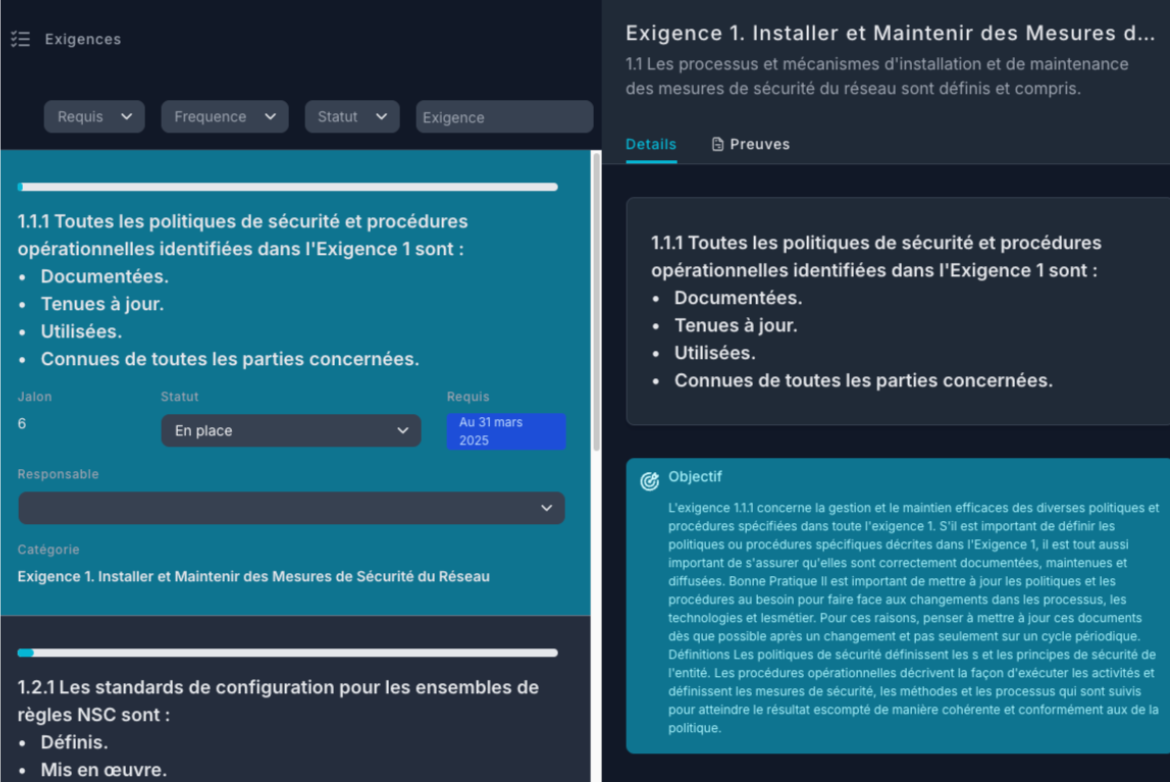
02
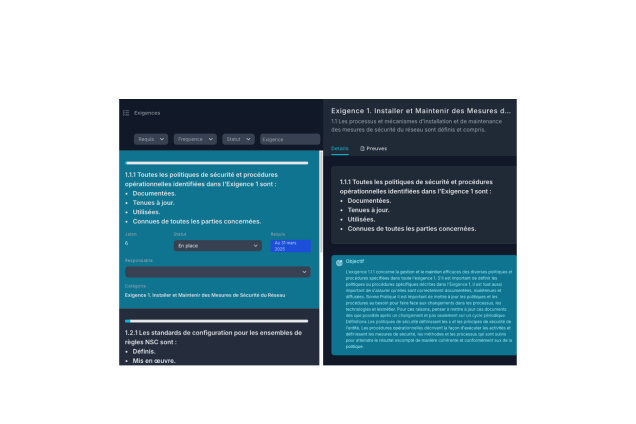
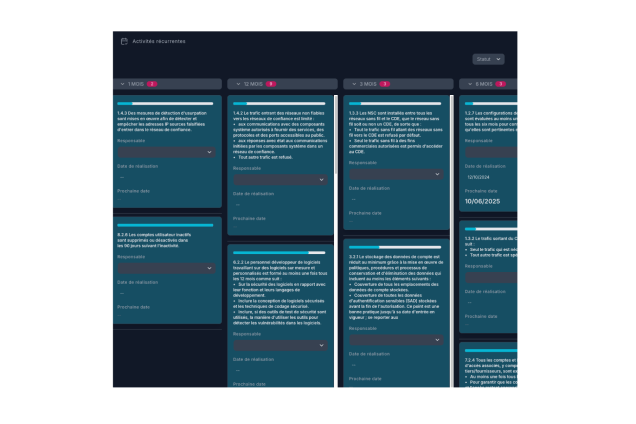
Suivi des exigences PCI DSS en temps réel
Visualisez l’état de chaque exigence avec un tableau de bord interactif.
Recevez des alertes automatisées pour éviter les retards.
03
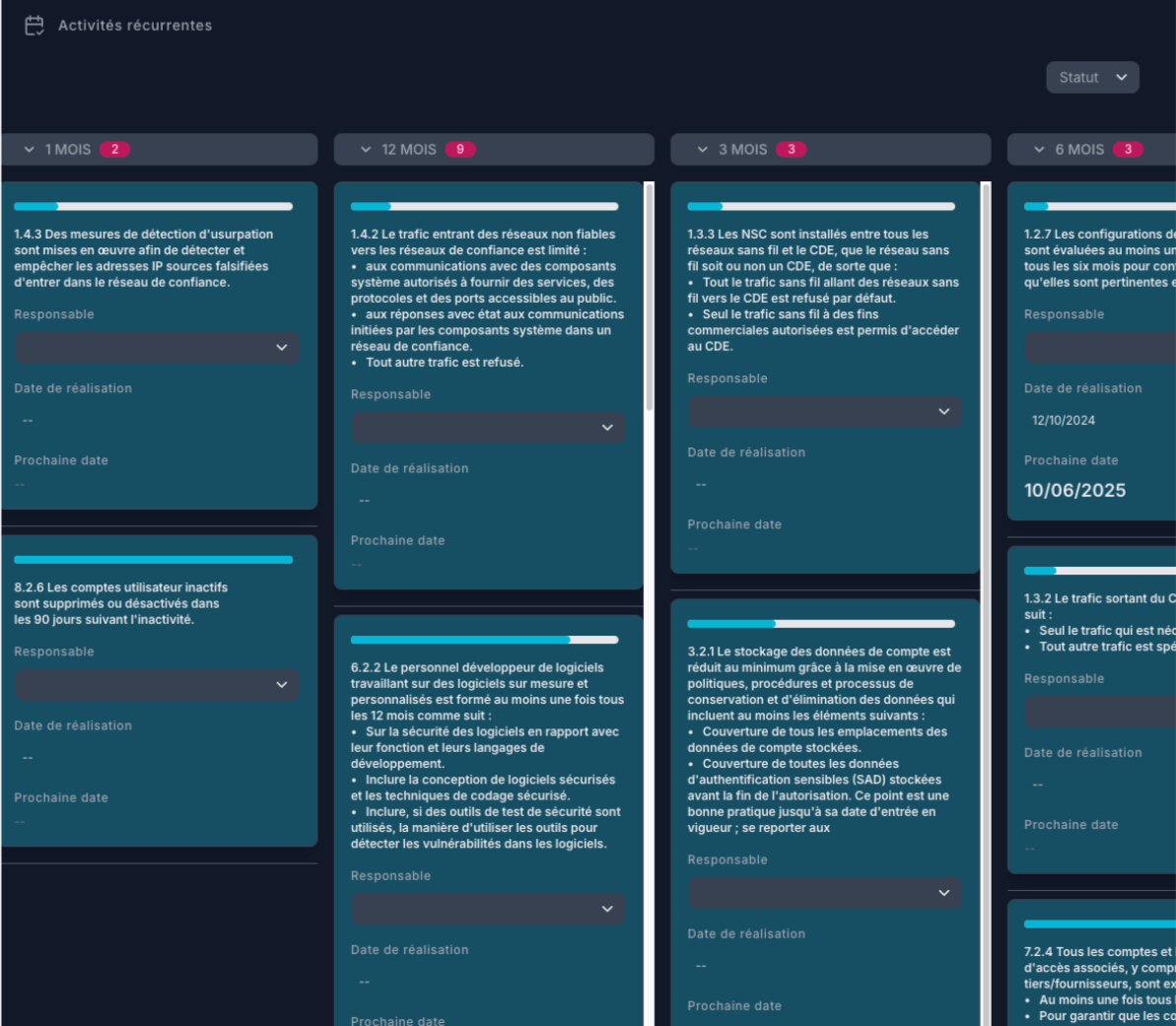
Automatisation des tâches récurrentes
Planifiez et automatisez les rappels pour les audits, les scans ASV, et les activités de maintenance.
04
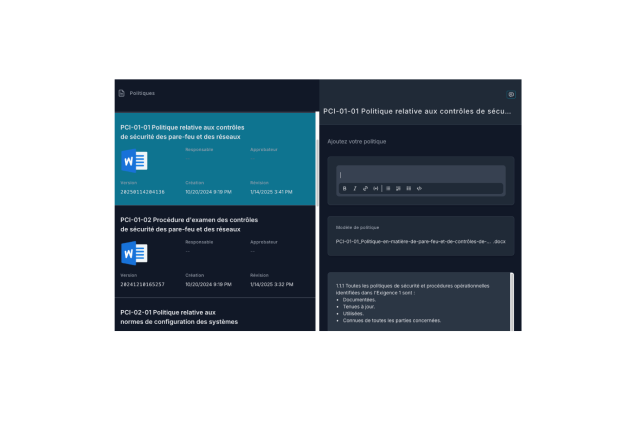
Collaboration et gestion centralisée
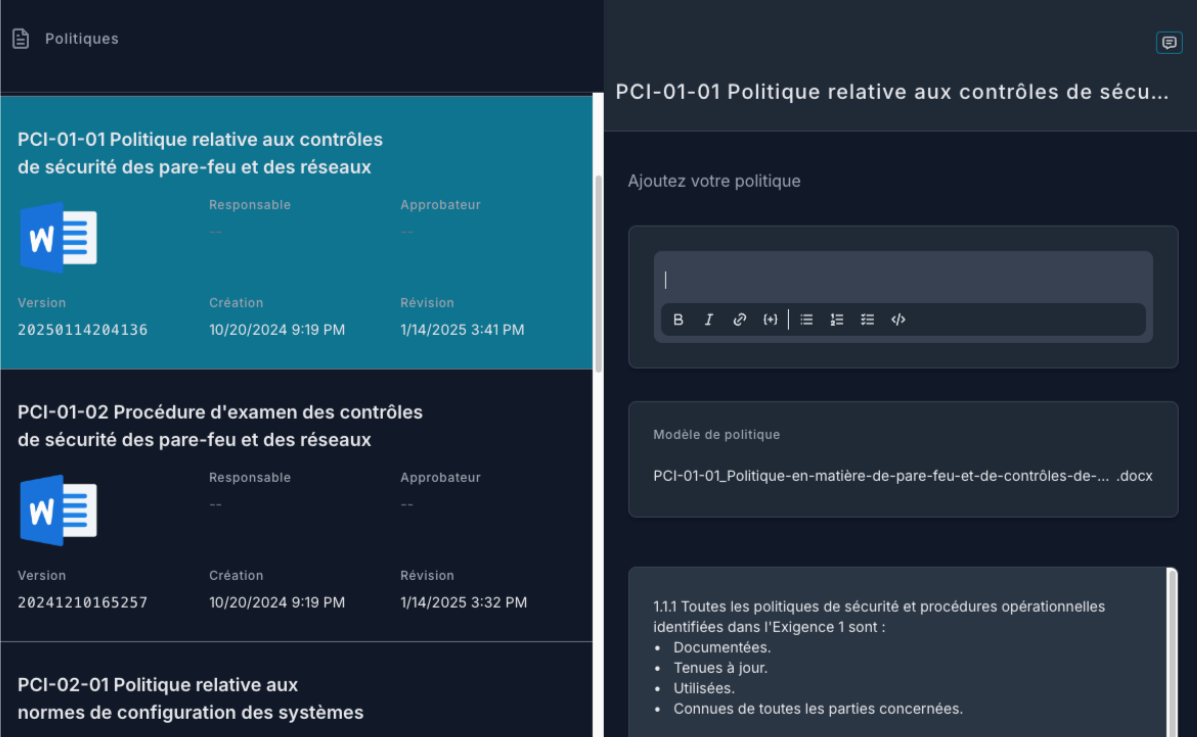
Modifiez, suivez et approuvez vos politiques avec une traçabilité complète.
Centralisez toutes les informations nécessaires pour vos audits.
05
Gestion de projet intégrée
Planifiez vos tâches avec un tableau Kanban intuitif.
Suivez les actions critiques et priorisez vos efforts.







La conformité PCIDSS:
simple, rapide... et intelligente.


Notre plateforme PCI 360
Les 6 objectifs principaux de PCI DSS
Construire et maintenir une infrastructure sécurisée.
Protéger les données des détenteurs de cartes.
Contrôler l’accès aux données sensibles.
Gérer les vulnérabilités des systèmes.
Adopter une politique de sécurité proactive.
Surveiller et tester les réseaux.
Les modules optionnels
Des extensions pour renforcer votre conformité selon vos besoins
01
Tests d'intrusion
Simulez des attaques réalistes pour tester vos défenses et corriger les failles avant qu’elles ne soient exploitées.
FONCTIONNALITÉS CLÉS :
-
Scénarios sur mesure selon votre environnement (app, réseau, API)
-
Test mené par des experts certifiés (OSCP, CREST, etc.)
-
Rapport détaillé avec recommandations stratégiques et techniques

02
Scans ASV (Approved Scanning Vendor)
Identifiez les vulnérabilités sur vos systèmes exposés à Internet et répondez aux exigences de PCI DSS avec des rapports officiels.
FONCTIONNALITÉS CLÉS :
-
Gestion des adresses IP et DNS
-
Planification automatique des scans
-
Rapport reconnu PCI DSS (trimestriel ou à la demande)
-
Recommandations techniques pour chaque faille identifiée

03
Certification annuelle (QSA)
Faites valider votre conformité officiellement par un QSA accrédité PCI DSS. Idéal pour les entreprises qui doivent fournir une attestation formelle à leurs partenaires ou institutions financières.
FONCTIONNALITÉS CLÉS :
-
Audit complet de vos systèmes, politiques et procédures
-
Préparation et accompagnement stratégique
-
Attestation de conformité PCI DSS (ROC & AOC)
.png)
FAQ
Vos Questions, Nos Réponses
Contrairement aux outils GRC généralistes ou aux solutions PCI fragmentées, PCI360 est spécialement conçu pour la conformité PCI DSS. Il ne s’agit pas d’un simple registre de contrôle : c’est une plateforme active, intelligente et opérationnelle.
Grâce à l’intégration de l’automatisation, de l’IA, de la gestion de projet intégrée et de la traçabilité complète, PCI360 permet aux équipes de gagner en efficacité, en rigueur, et en coordination, tout en garantissant une documentation claire pour les audits.PCI DSS est souvent le premier jalon vers une sécurité plus structurée. PCI360 vous permet de :
-
Identifier rapidement les lacunes structurelles ou techniques
-
Implémenter une hygiène de sécurité dans les processus récurrents (journalisation, segmentation, gestion des accès)
-
Alimenter des indicateurs stratégiques utiles pour des démarches ISO 27001, SOC 2, ou NIST
C’est donc plus qu’un outil de conformité : c’est un levier d’amélioration continue et de standardisation de vos pratiques.
-
La plateforme est conçue pour favoriser l’alignement interfonctionnel :
-
Gestion des rôles et des accès
-
Attribution de tâches, validation de documents et suivi des responsabilités
-
Journalisation complète des actions pour responsabiliser chaque acteur
-
Vue stratégique pour les gestionnaires et opérationnelle pour les techniciens
Résultat : moins de silos, plus de fluidité et d’adhésion au processus.
-
L’offre Entreprise de PCI360 est pensée pour les environnements distribués :
-
Création de sous-entités, unités d’affaires ou groupes de sites
-
Gestion centralisée ou déléguée des politiques et preuves
-
Export et consolidation des audits par filiale ou par région
-
Intégration avec vos solutions globales (LDAP, SIEM, etc.)
Cela permet une standardisation à l’échelle du groupe, sans perdre en autonomie locale.
-
En moyenne, nos clients constatent :
-
Une réduction de 30 à 50 % du temps passé sur les processus de conformité
-
Une meilleure visibilité sur la posture PCI DSS en temps réel
-
Une diminution du risque d’échec à l’audit ou de non-conformité aux SAQ
-
Un alignement renforcé entre IT, sécurité, conformité et gestion
Au-delà de la conformité, PCI360 accélère la maturité cybersécuritaire de votre organisation.
-
Les feuilles Excel, outils de ticketing ou plateformes GRC internes montrent vite leurs limites pour PCI DSS.
PCI360 :-
S’intègre à vos systèmes existants via API (SIEM, IAM, ITSM, etc.)
-
Centralise les preuves, politiques et actions en un seul endroit
-
Automatise les tâches fastidieuses pour libérer vos équipes
En bref, PCI360 ne remplace pas, il renforce votre arsenal en ciblant un domaine très spécifique avec une approche experte.
-
L’intelligence artificielle dans PCI360 n’est pas cosmétique. Elle est conçue pour :
-
Analyser votre progression et détecter les écarts critiques
-
Suggérer automatiquement les prochaines actions à prioriser
-
Croiser les exigences avec vos preuves pour détecter les manques ou redondances
-
Vous assister dans le choix du SAQ adapté et dans l’interprétation des exigences
L’IA agit comme un conseiller embarqué, accélérant les décisions sans jamais retirer le contrôle aux utilisateurs.
-
Justement parce que le travail de votre QSA ou consultant sera largement facilité. PCI360 :
-
Structure la préparation à l’audit, réduisant les échanges et les erreurs
-
Centralise les preuves et politiques nécessaires à l’attestation
-
Évite les pertes de temps liées aux relances, aux documents manquants ou aux versions obsolètes
Beaucoup de QSA recommandent PCI360 pour accélérer la collecte d’information, fiabiliser les livrables et éviter les allers-retours inutiles.
-
.png)
Devenez Partenaire 🤝
Vous êtes consultant en cybersécurité, intégrateur, MSP ou cabinet de conformité ?
Offrez plus de valeur à vos clients en intégrant PCI360 à votre portefeuille de services.
En devenant partenaire revendeur, vous bénéficiez de :
-
Accès privilégié à une plateforme SaaS intelligente et intuitive dédiée à la conformité PCI DSS.
-
Conditions préférentielles et marges attractives sur chaque abonnement revendu.
-
Un portail partenaire pour gérer vos clients, accéder aux supports, ressources techniques et documents marketing.
-
Un accompagnement commercial et technique dédié pour vous aider à réussir.
Proposez une solution clé en main à vos clients, simplifiez leur conformité et démarquez-vous sur le marché avec PCI360.

Ce que nos clients disent
témoignage

This is your Testimonial quote. Give your customers the stage to tell the world how great you are!
Frankie B.
Poste

This is your Testimonial quote. Give your customers the stage to tell the world how great you are!
Jesse N.
Poste

This is your Testimonial quote. Give your customers the stage to tell the world how great you are!
Jamie L.
Poste
Tarification
Une solution pour chaque type d’entreprise
Offre Essentielle
Idéale pour les petites entreprises ou celles qui entament leur démarche de conformité
INCLUS :
-
Assistant intelligent pour identifier le bon SAQ
-
Suivi en temps réel de la conformité
-
Tableaux de bord interactifs
-
Automatisation des rappels et tâches récurrentes
-
Gestion documentaire et approbation de politiques
-
Gestion de projet intégrée (Kanban, priorisation)
-
Support standard par courriel
À partir de 499 $/mois.
Offre Professionnelle
Pensée pour les PME en croissance, cette offre ajoute des fonctionnalités de collaboration avancée et de gestion multi-parties prenantes.
Tout dans l’offre Essentielle, plus :
-
Collaboration entre équipes internes et externes
-
Gestion des partenaires tiers et fournisseurs
-
Export de rapports pour audits internes et documentation
-
Gestion étendue des utilisateurs et des rôles
-
Support prioritaire (courriel + chat)
À partir de 999 $/mois.
Offre Entreprise
Parfaite pour les grandes entreprises, groupes multisites ou environnements réglementés.
Tout dans l’offre Professionnelle, plus :
-
Accès à l’API PCI360 (intégration SIEM, IAM, ticketing, etc.)
-
Fonctions avancées pour la gouvernance et les audits globaux
-
Environnements multi-entités et hiérarchie personnalisée
-
Support 24/7 avec un conseiller dédié

.jpg)